CloudSek CTF Writeup
Here is how I solved the CTF Challenge from CloudSek. I managed to finsih in the top 10 even though i took 3 hrs to solve this. I learned about PHP Type Juggling from this challenge.
CHALLENGE
The challenge starts with the LINK to a website which looks like this:

Since there is nothing interesting on the page, let’s start haxoring! The first thing to check is for the robots.txt and luckily we got some juicy info.
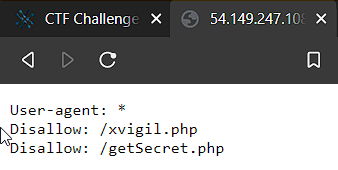
On visiting xvigil.php got php script which is taking two inputs hash and xvigil
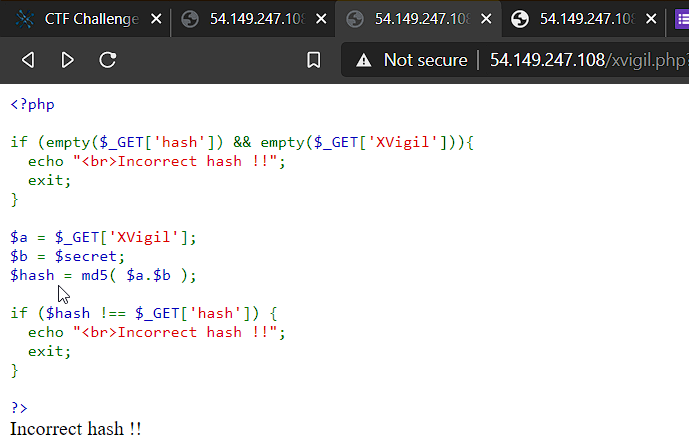
Lets check getSecret.php out. We got another php script this script is taking two inputs Cl0ud and SEK and then converting the values of these two to md5 and then checking if the md5 values of two variable is equal. If the values are then it will print out the secret.
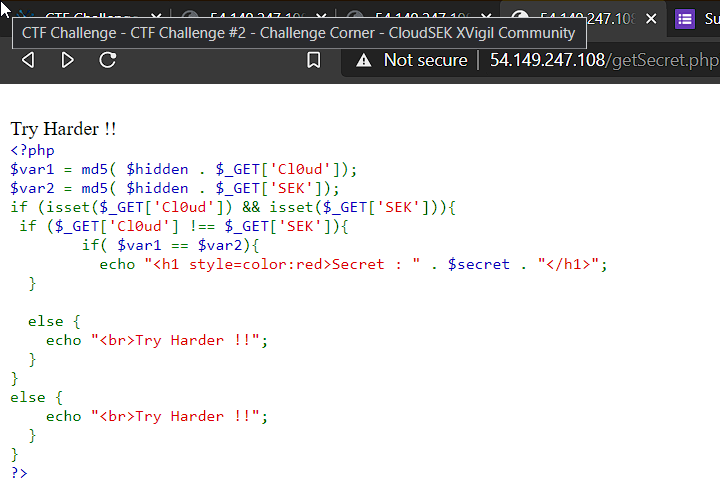
Now how can two different values have same md5 hash? So I fired up google and searched how can i make two md5 hash equal in php and i found this blog post about [PHP Type Juggling] (https://www.netsparker.com/blog/web-security/php-type-juggling-vulnerabilities/). After reading this post i got to know that there is a vulnerability in php that allows it to evaluate two values of different data types to true if there hash is in the scientific E-notation format. So Passed the values ‘240610708 and ‘QNKCDZO’ to the two variables.
We got the secret thanks to php type juggling.
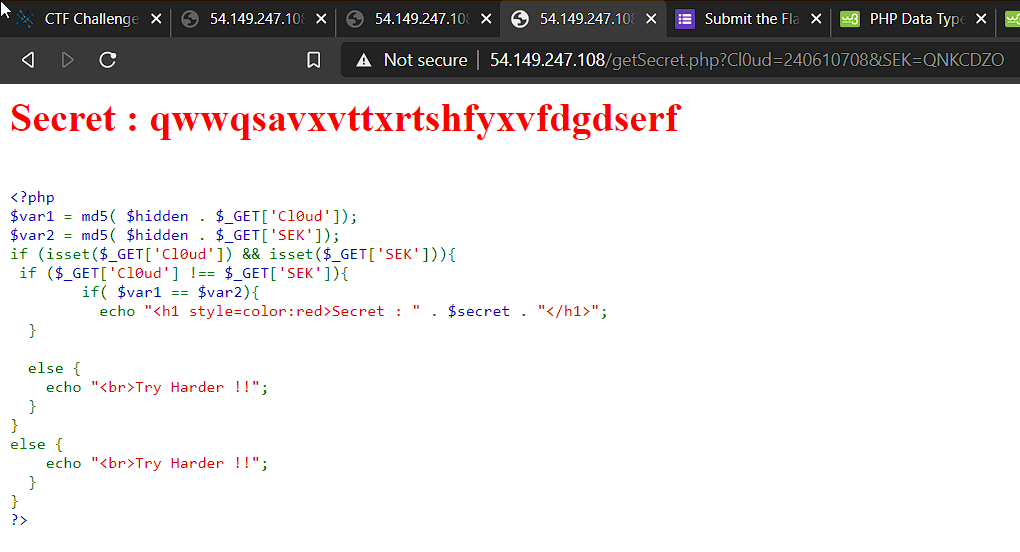
Now we have to pass the md5 hash of secret and the string in xvigil variable as the value of hash variable in xvigil.php script. For eg: I passed Xvigil = ctf and Hash = 3fb855e61ae87fd72739c50b5dcbd323. Here value of Xvigil can be anything bt the value of hash will be md5 hash of ‘value in Xvigil + Secret’.
And on doing the above action the php script evaluates to true and we got our flag and the link to google form where we have to submit the flag.
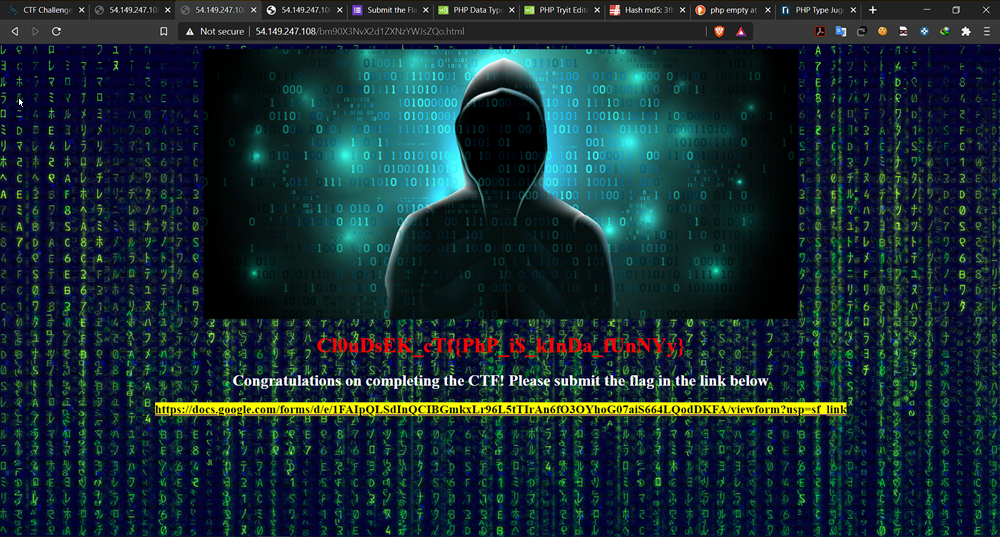
FLAG: Cl0uDsEK_cTf{PhP_i$_kInDa_fUnNYy}
All articles in this blog except for special statements,Both adopt CC BY-SA 4.0 protocol, Please indicate the source!