CyberYoddha CTF Writeup
I played this CTF as a solo player and i finished 84th/727 teams. It was great fun participating in this CTF. Let’s see how I solved some challenges.
WELCOME
Welcome
Type “?flag” in the discord server, carlbot would DM you the flag.
FLAG: CYCTF{W3lc0m3_t0_Cyb3rY0ddh@_CTF_2020!}
TRIVIA
Trivia 1
FLAG: Linus Torvalds
Trivia 2
FLAG:Gary Kildall
Trivia 3
FLAG: Yahoo
Trivia 4
FLAG: Honeypot
Trivia 5
FLAG: Shoulder Surfing
Trivia 6
FLAG: Logic Bomb
Trivia 7
FLAG: System File Checker
Trivia 8
LOGO:

FLAG: Haskell
SHEBANG
Shebang0
As the challenge description says we have to connect to the server via ssh for solving these challenges.
1 | |
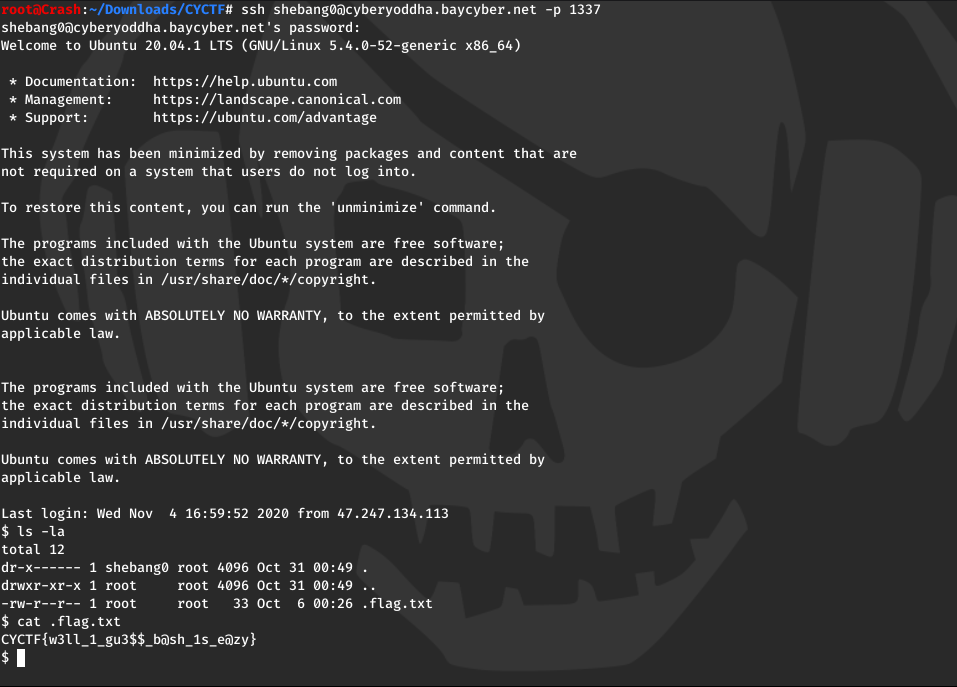
FLAG: CYCTF{w3ll_1_gu3$$_b@sh_1s_e@zy}
Shebang1
1 | |
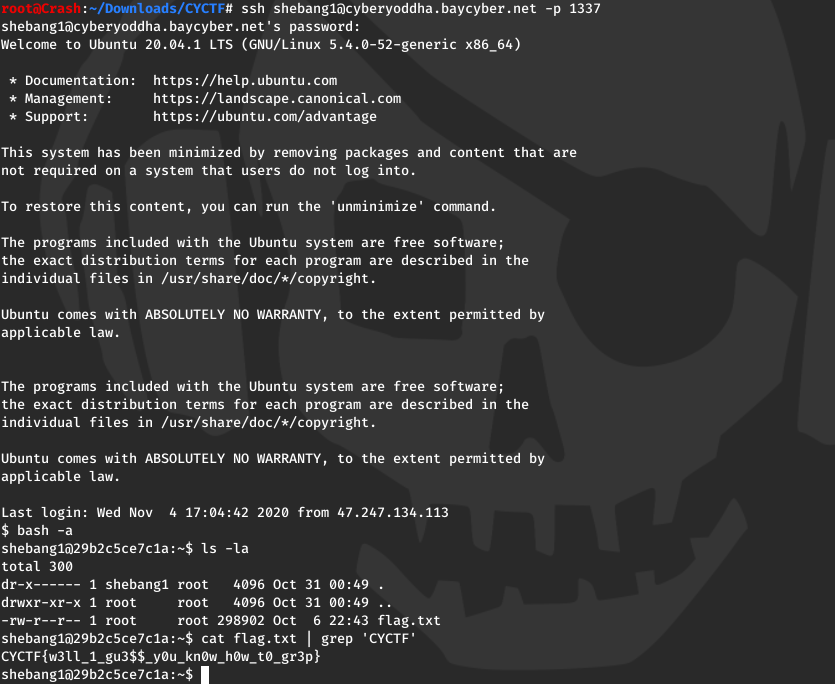
FLAG: CYCTF{w3ll_1_gu3$$_y0u_kn0w_h0w_t0_gr3p}
Shebang2
1 | |
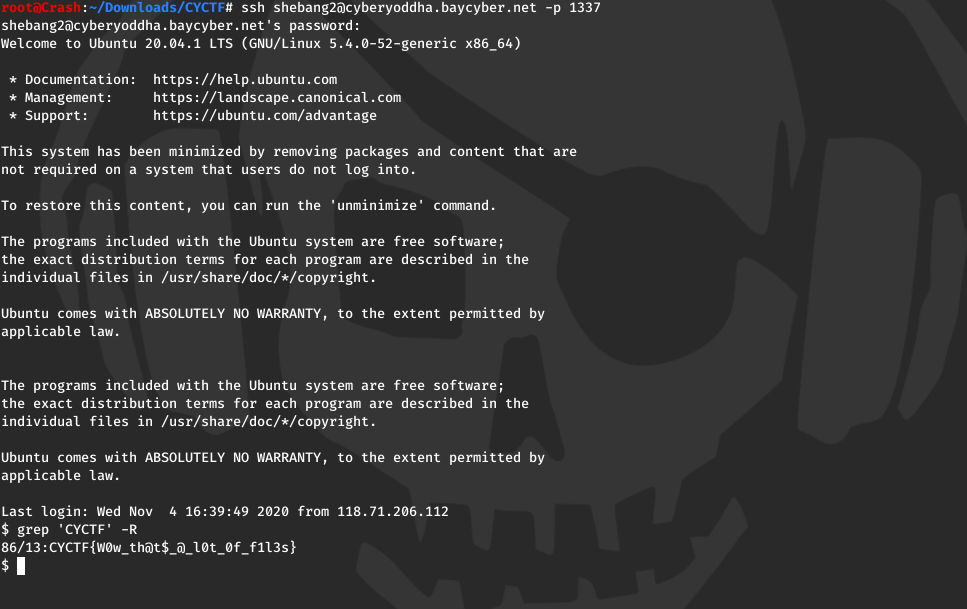
FLAG: CYCTF{W0w_th@t$_@_l0t_0f_f1l3s}
Shebang3
1 | |
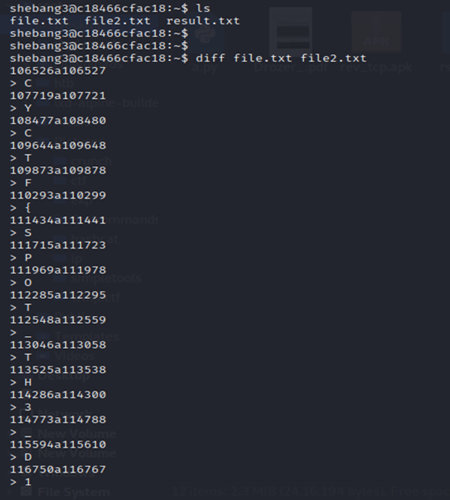
FLAG: CYCTF{SPOT_TH3_D1FF}
Shebang4
1 | |
FLAG: CYCTF{W3ll_1_gu3$$_th@t_w@s_actually_easy}
WEB EXPLOITATION
Look Closely
On opening the link we got:
On searching for “cyctf” on the source page i got the flag.
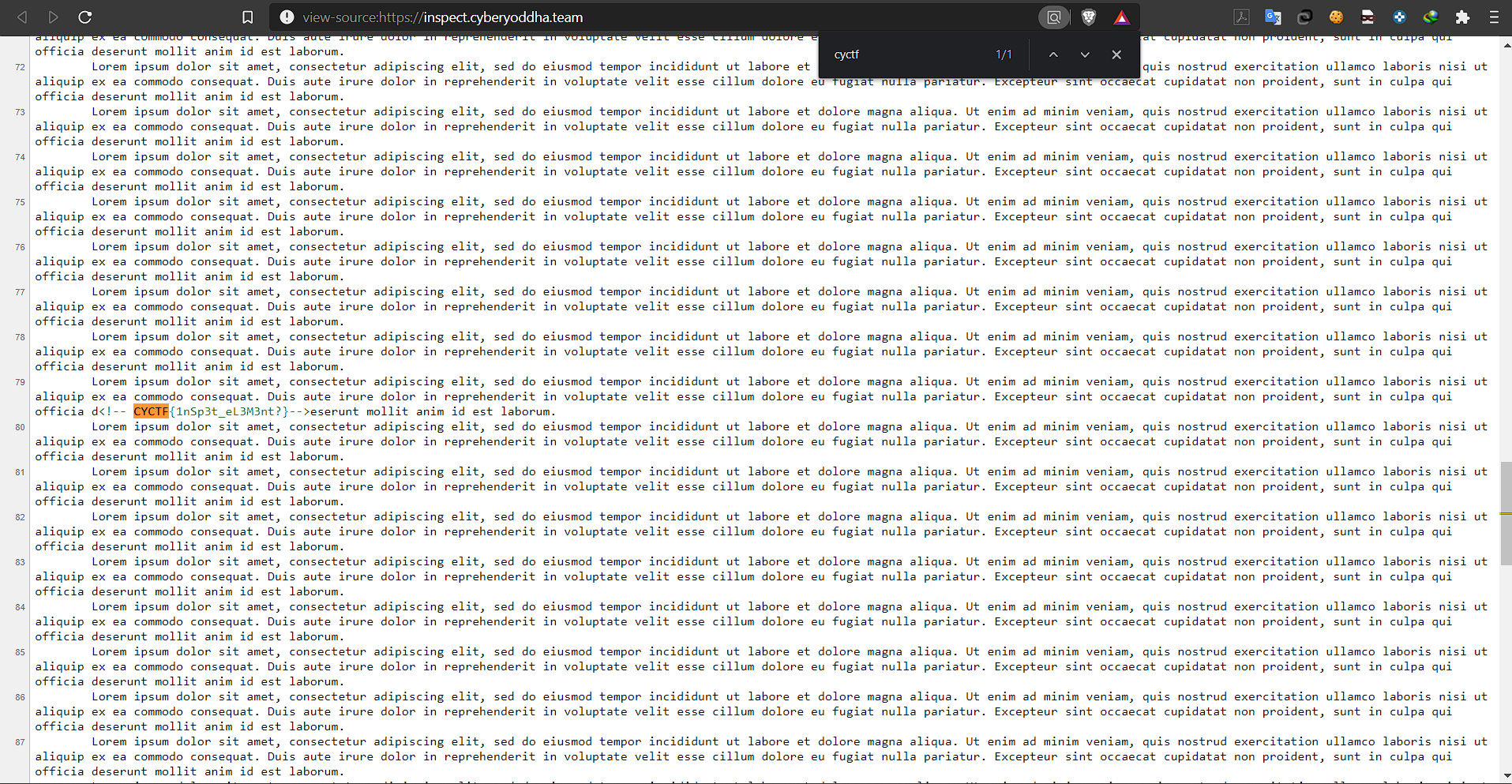
FLAG: CYCTF{1nSp3t_eL3M3nt?}
Disallow
On visiting link i was presented with this page:
So challenge name is Disallow so the first thought that comes to mind is to search for the robots.txt file. ( robots.txt file contain disallow feature)
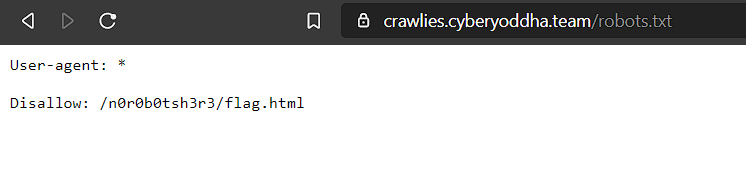
Got the flag by opening the link found in robots.txt.
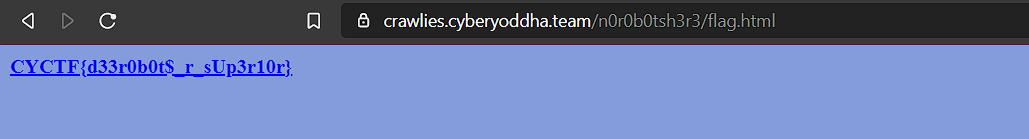
FLAG: CYCTF{d33r0b0t$_r_sUp3r10r}
Data Store
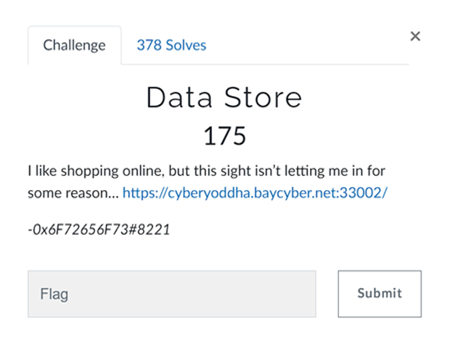
On Visiting the link we are presented with a Login Page.
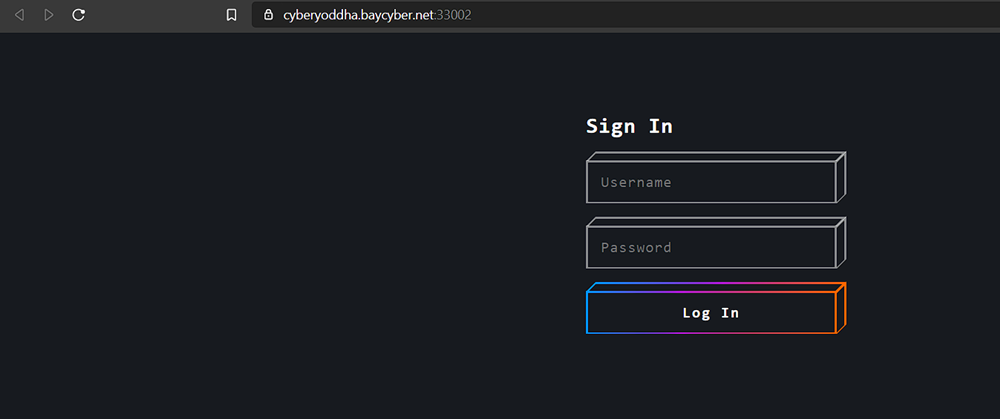
First thing i tried is default username and password like “Admin:Password” this didn’t work
the second thing that came to my mind is SQL Injection so i started trying SQLi Payloads and
the “admin ‘ OR 1 – -“ got me logged in.
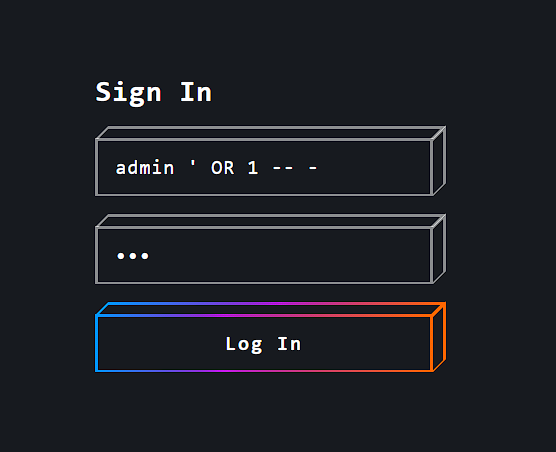
On the next page i got the flag.
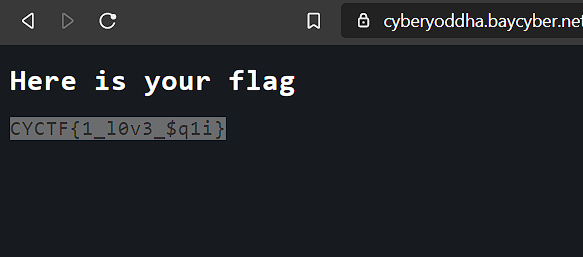
FLAG: CYCTF{1_l0v3_$q1i}
Something Sw33t
On visiting the link i got this page:
After checking the source code i found nothing. Then i looked at the cookies for this webpage and found a intresting cookie named “don’t look here”.
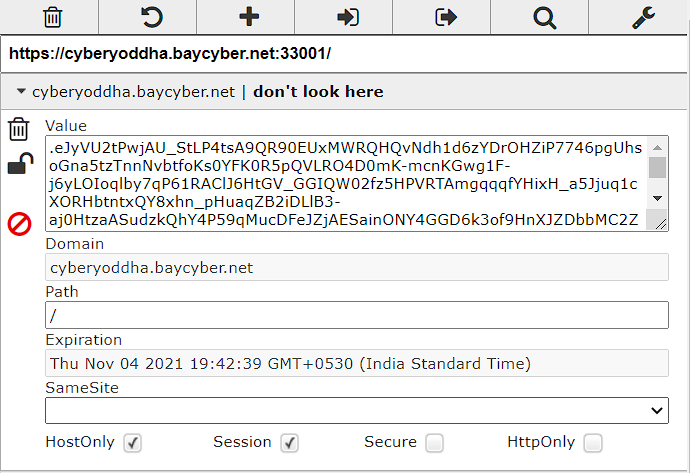
On inspecting the cookie i came to know that it is a flask cookie so i used a “flask-unsign” a tool which decodes the flask cookies. On decoding the cookie i found a bunch of base4 encoded strings.
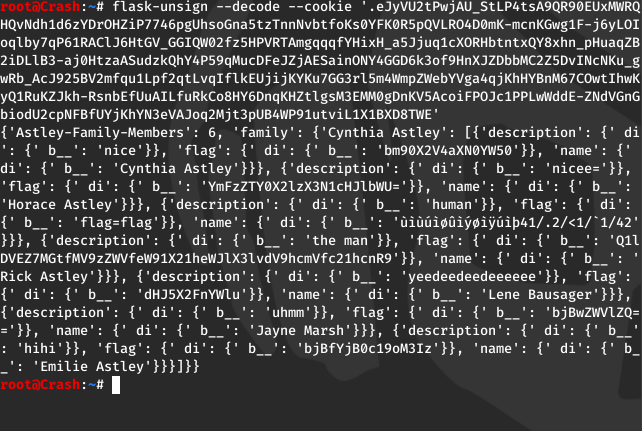
On decoding these base64 encoded strings i got the flag.
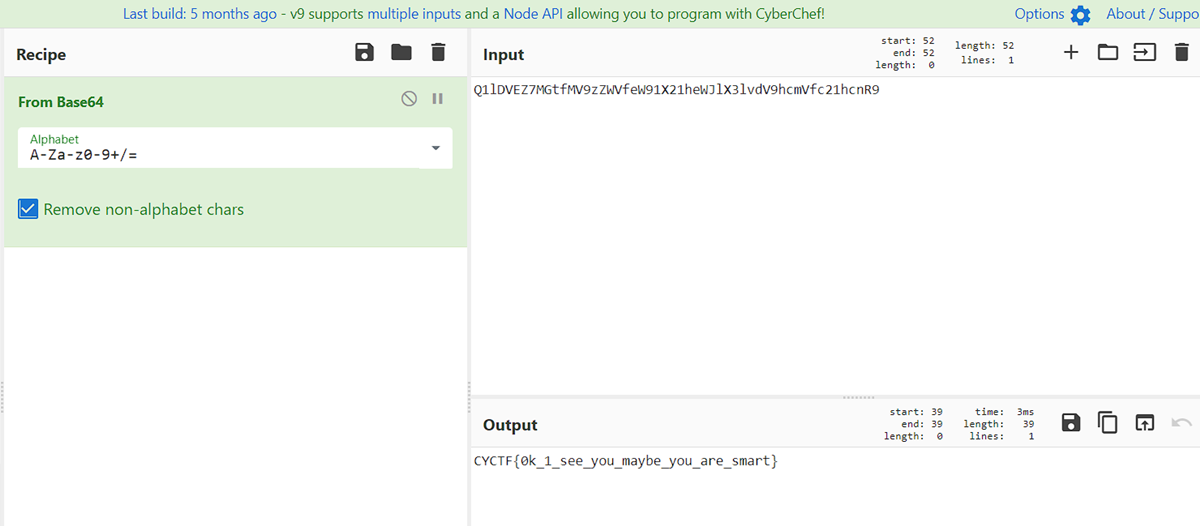
FLAG: CYCTF{0k_1_see_you_maybe_you_are_smart}
Data Store 2
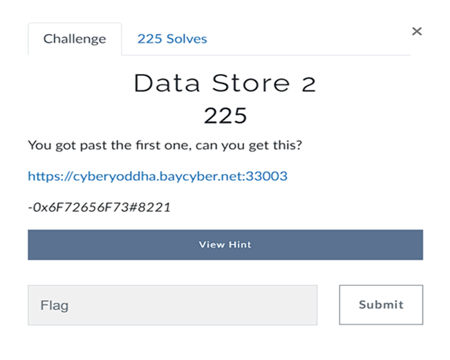
On visiting the link i got the same login page as the Data Store challenge
This time a file was provided on reading which i got to know that this the username field is sanitised and thus cannot be used for SQLi.
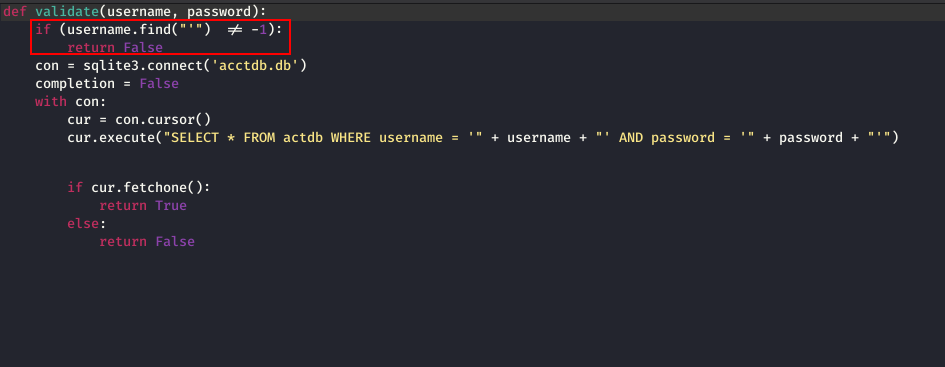
Using the same payload used in previous challenge in the password field got me logged in.
On the next page i got the flag.
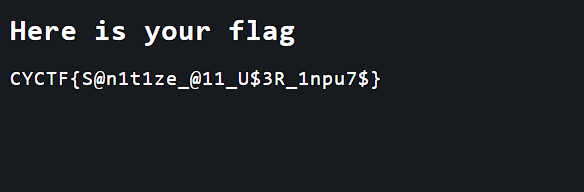
FLAG: CYCTF{S@n1t1ze_@11_U$3R_1npu7$}
Data Store 3
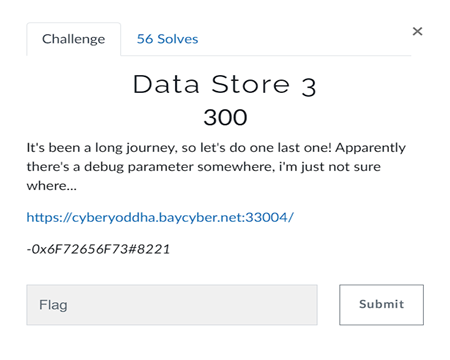
On visiting the link i got a login page with a single password field
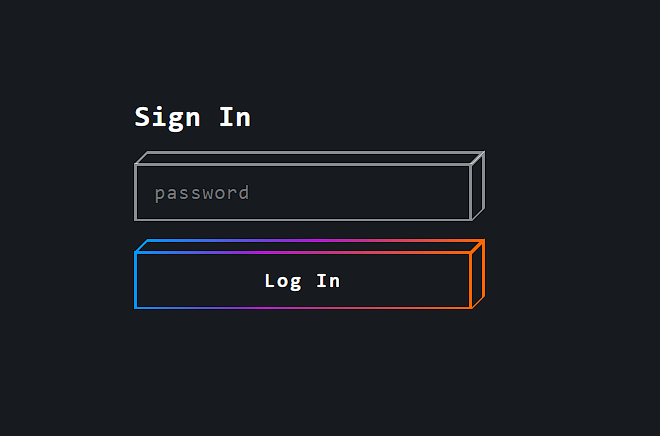
Using the payload “‘=0–+” in the password field got me logged in.
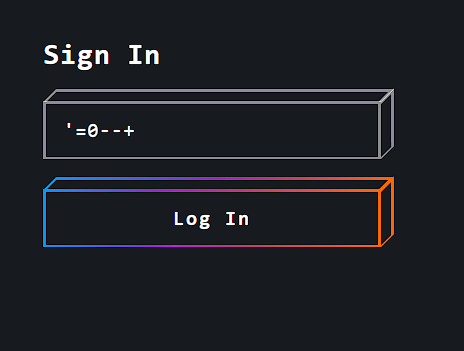
On the next page i got the Flag.
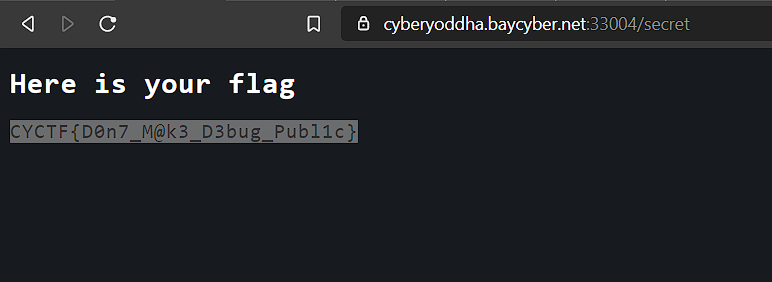
FLAG: CYCTF{D0n7_M@k3_D3bug_Publ1c}
CRYPTO
Beware the Idles of March
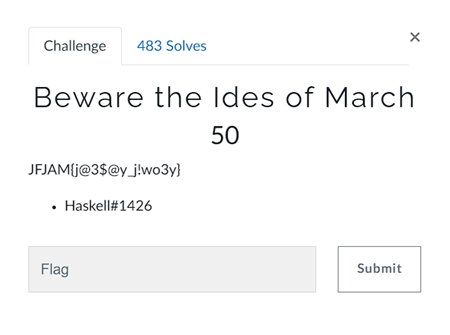
It looks like a rotation cipher so put the string “JFJAM{j@3$@y_j!wo3y}” in cyberchef and applied Rotation,on the rotation of 19 got the flag.
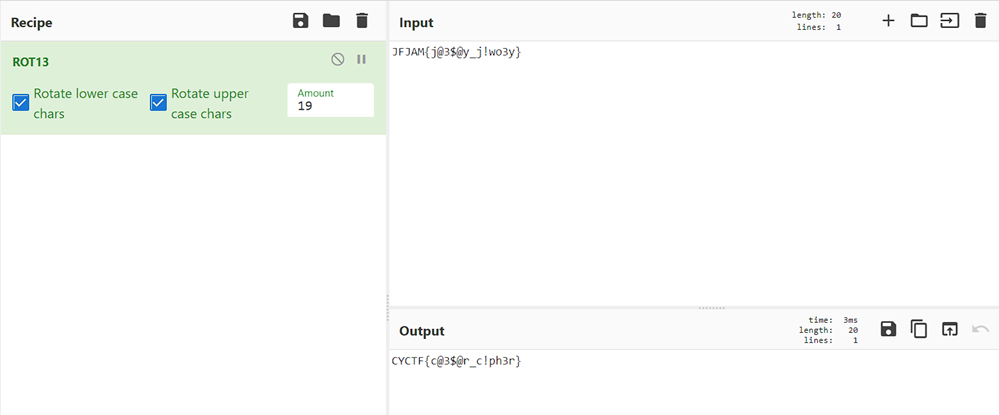
FLAG: CYCTF{c@3$@r_c!ph3r}
Home Base
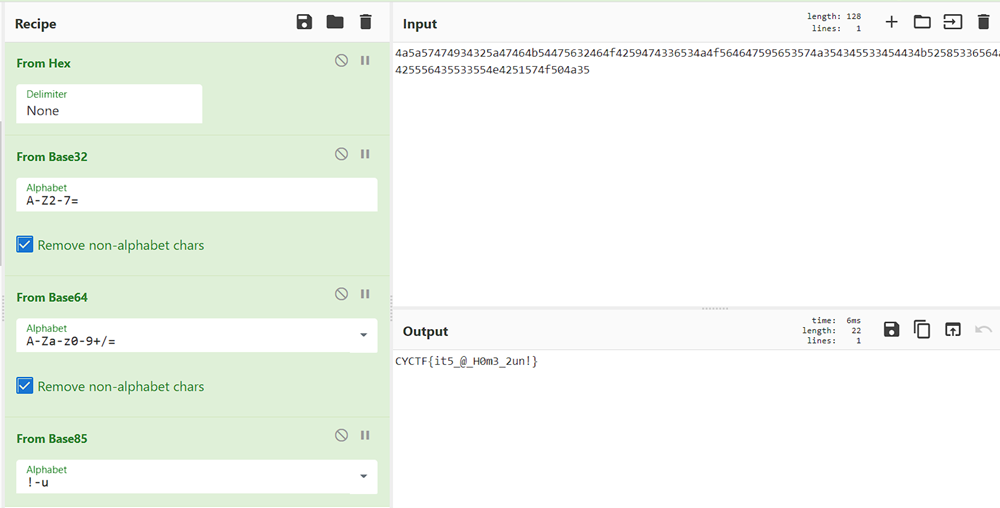
Put the string in cyberchef and converted it From Hex > Base 32 > Base 64 > Base 85, and got the flag.
FLAG: CYCTF{it5_@_H0m3_2un!}
Sus
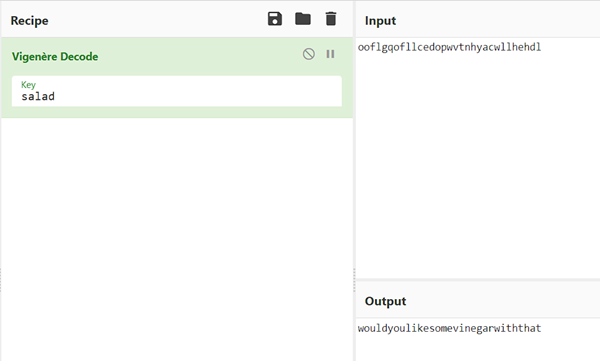
The Hint gives the idea that it can be vigenere cipher so i put the string “ooflgqofllcedopwvtnhyacwllhehdl” in cyberchef and used vigenere decoder and got the flag. Key is SALAD but you can just do auto decryption at dcode.fr to get “wouldyoulikesomevinegarwiththat”.
FLAG: CYCTF{wouldyoulikesomevinegarwiththat}
Rak 1
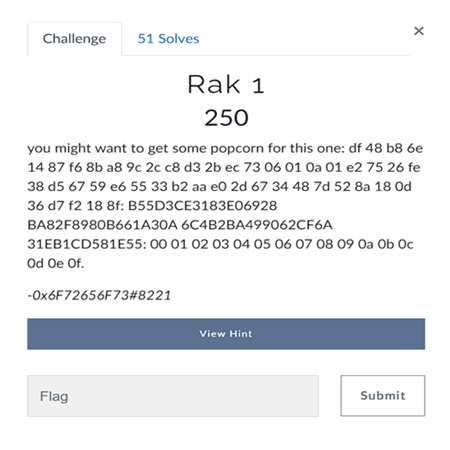
The Hint tells that it is an Advanced encryption, so in cyberchef i tried AES decode and got the flag.
- Cipher Text = “df 48 b8 6e 14 87 f6 8b a8 9c 2c c8 d3 2b ec 73 06 01 0a 01 e2 75 26 fe 38 d5 67 59 e6 55 33 b2 aa e0 2d 67 34 48 7d 52 8a 18 0d 36 d7 f2 18 8f”
- Key = “B55D3CE3183E06928 BA82F8980B661A30A 6C4B2BA499062CF6A 31EB1CD581E55”
- IV = “00 01 02 03 04 05 06 07 08 09 0a 0b 0c 0d 0e 0f”
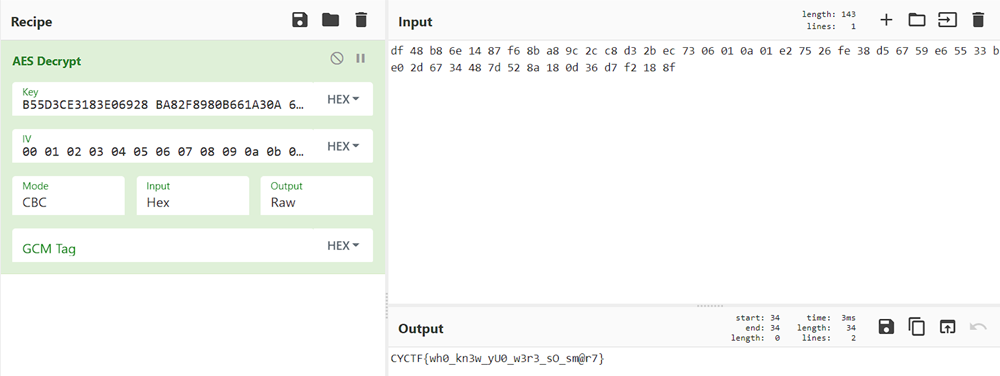
FLAG: CYCTF{wh0_kn3w_yU0_w3r3_sO_sm@r7}
MISC
Lorem Ipsum
I compared the given text with original Lorem ipsum text and found that there are some words which are extra in the given text. So After comparing the whole text i got cyctflatiniscool which is our flag.
FLAG: cyctf{latiniscool}
FORENSICS
Image Viewer
Used Exiftool on the image and got the flag.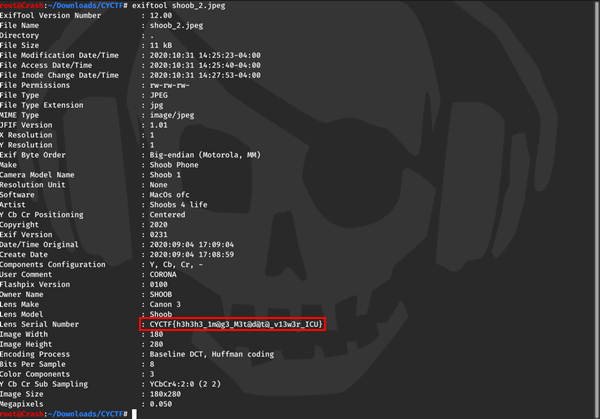
FLAG: CYCTF{h3h3h3_1m@g3_M3t@d@t@_v13w3r_ICU}
The row beneath
1 | |
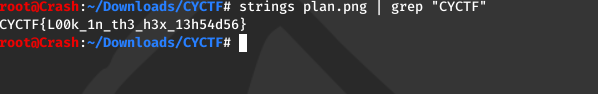
FLAG: CYCTF{L00k_1n_th3_h3x_13h54d56}
What’s the password?
Used “steghide extract -sf sudo.jpg” with “sudo” as password to get flag.
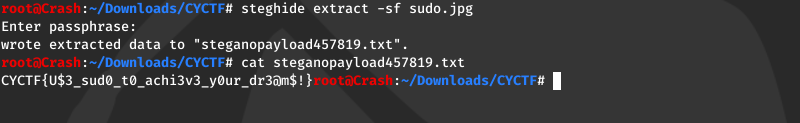
FLAG: CYCTF{U$3_sud0_t0_achi3v3_y0ur_dr3@m$!}
Flag delivery
Replaced characters with . and - since it is morse code, used morse decoder and got the flag.
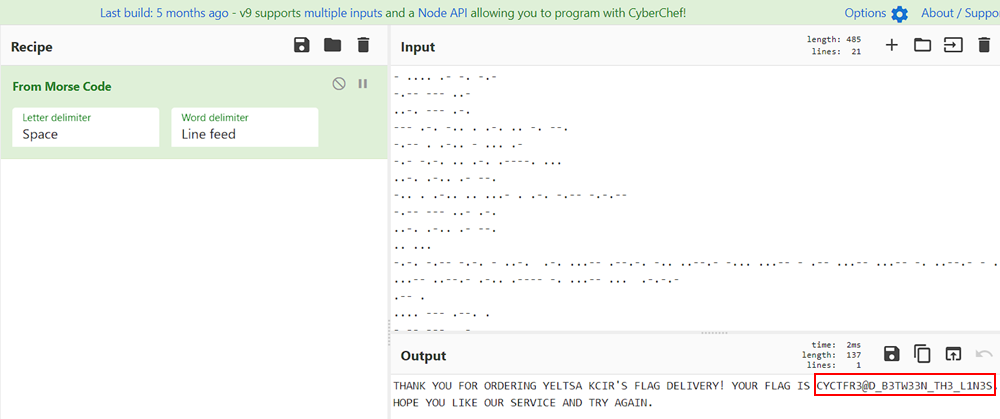
FLAG: CYCTF{R3@D_B3TW33N_TH3_L1N3S}
Flag delivery 2
The challenge gave us a corrupted file and on opening it in the hex editor i got to know that it is a png file, so i fixed the wrong header and the data part.
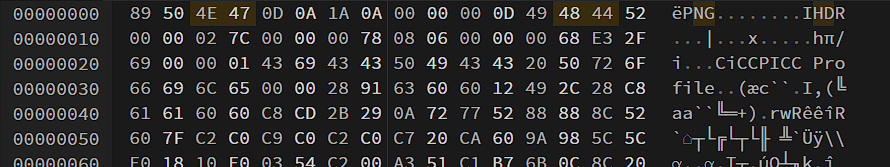
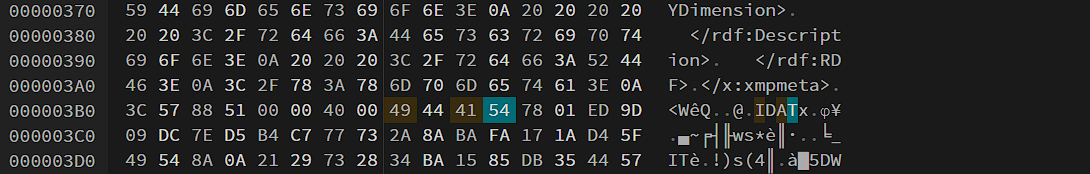
I got the flag after exporting the file from hex editor.
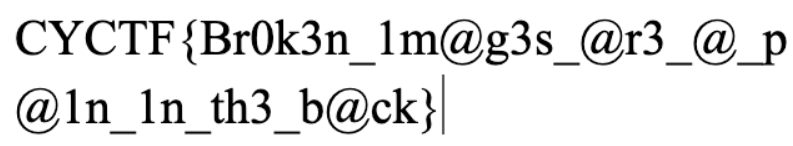
FLAG: CYCTF{Br0k3n_1m@g3s_@r3_@_p@1n_1n_th3_b@ck}
Steg 2
I used stegsolve and changed the colour plane found the flag in Red Plane 1.
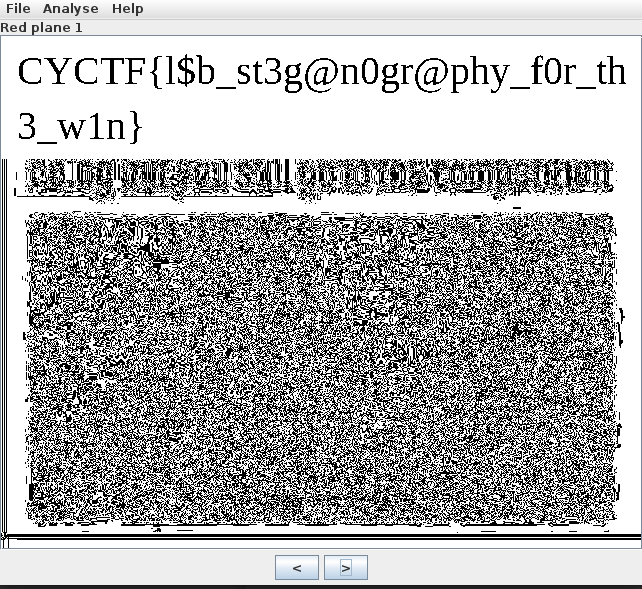
FLAG: CYCTF{l$b_st3g@n0gr@phy_f0r_th3_w1n}
Steg Ultimate
First i used steghide to extract a text file embedded in given image.
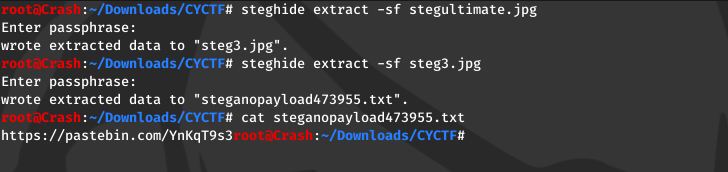
The embedded file gave a link which gave us base64 encoded strings.
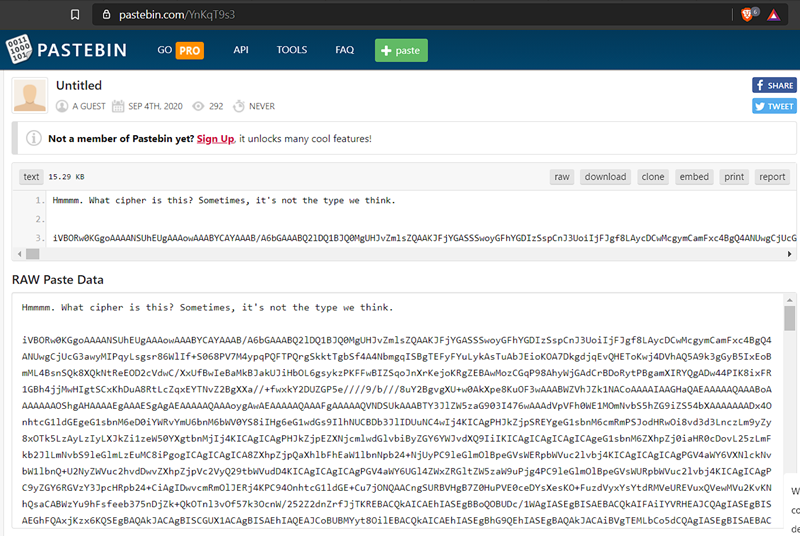
When i converted the base64 encoded string to file with a online decoder i got the flag.
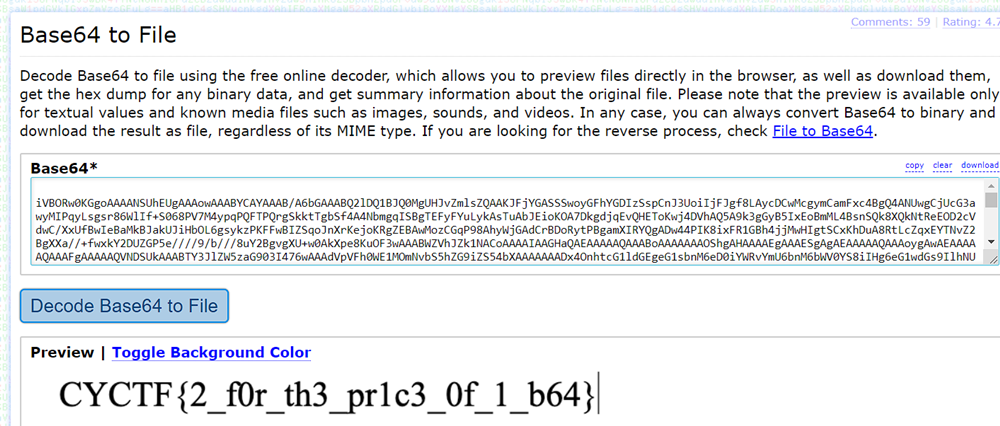
FLAG: CYCTF{2_f0r_th3_pr1c3_0f_1_b64}
REVERSE ENGINEERING
Password 1
Challenge provides the following code:
1 | |
I changed the code to the following code and got the flag.
1 | |
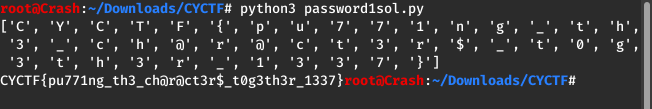
FLAG: CYCTF{pu771ng_th3_ch@r@ct3r$_t0g3th3r_1337}
Password 2
Challenge provides the following code:
1 | |
I changed the code to the following code and got the flag.
1 | |
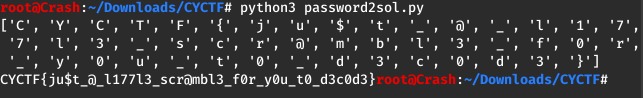
FLAG: CYCTF{ju$t_@_l177l3_scr@mbl3_f0r_y0u_t0_d3c0d3}
PASSWORD CRACKING
secure (I think?)
I used crackstation on the given hash and got the flag.
.png)
FLAG: securepassword
Crack the Zip!
Run “fcrackzip -Du -p /usr/share/wordlists/rockyou.txt flag.zip” on the given zip and i got the password for the zip, opened the zip and got the flag in the file inside the zip.
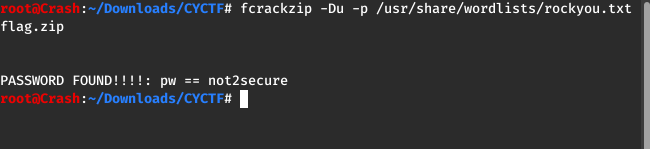
FLAG: cyctf{y0u_cr@ck3d_th3_z!p…}
supa secure
Run “hashcat -m 20 -a 0 -o cracked.txt hash.txt /usr/share/wordlists/rockyou.txt –force” with [given hash]:[given salt (cyctf)] in the hash.txt gets the flag.
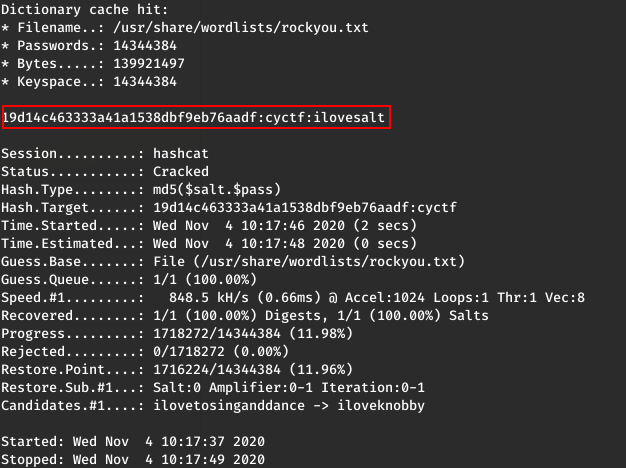
FLAG: cyctf{ilovesalt}
Me, Myself, and I
Used crackstation on the given hash

FLAG: CYCTF{whoami}
All articles in this blog except for special statements,Both adopt CC BY-SA 4.0 protocol, Please indicate the source!